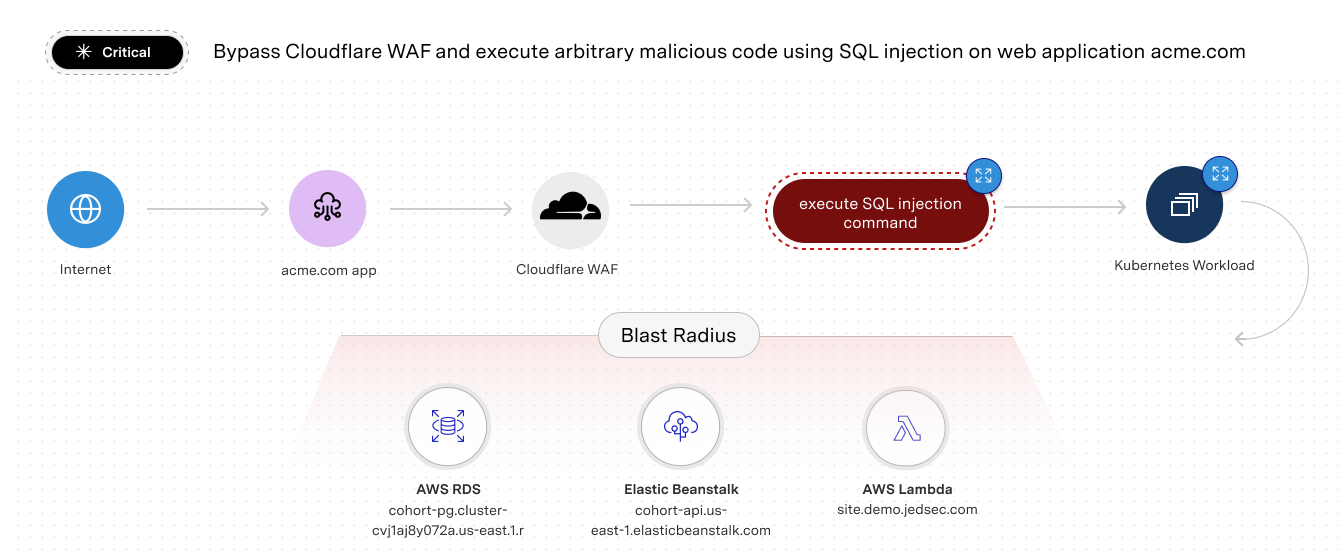
Stop wasting time resolving
Security
Alerts
that don’t matter
Know if
you’re exposed
With continuous monitoring, Jed searches for exploitable vulnerabilities and misconfigurations to answer the vital question, “Are you exposed to an attack?”
Learn more →
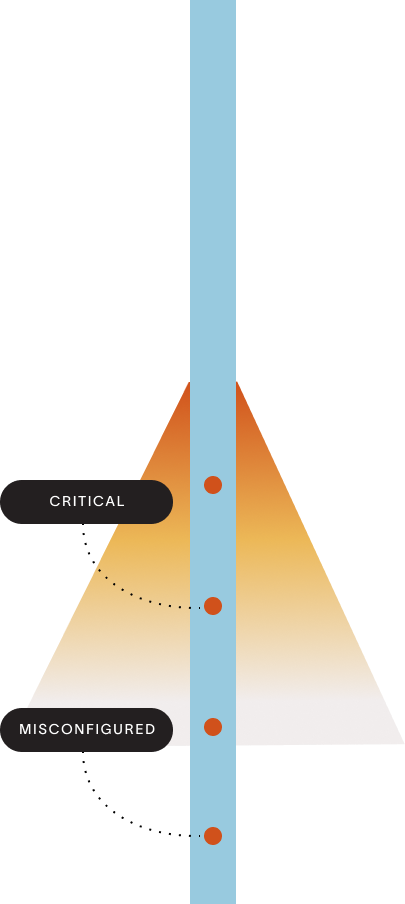
Validate threats
and focus mitigation
We combine multiple security findings into individual threats. Prioritized by what’s likely to occur and could do the most damage –helping you focus your efforts.
Learn more →




Turn threats
into action
We streamline operational processes, and provide clear and minimal remediation steps, so you can transform threats into tasks in minutes.
Learn more →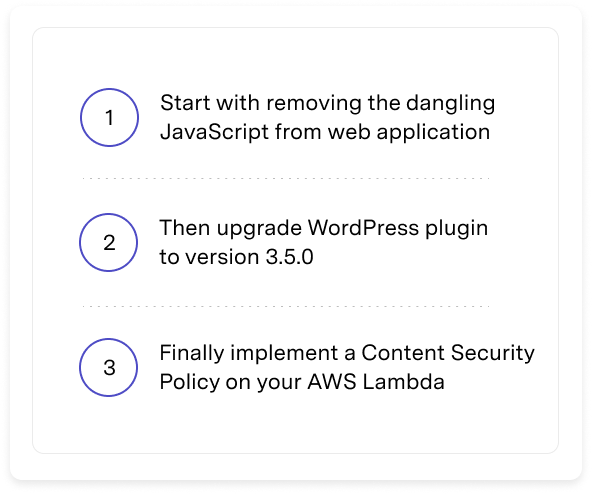

Discover your entire
threat landscape